Which of the Following Best Describes a Memory Leak
A defect leading to resource exhaustion of which only C Memory leak fits that descriptor. Determining Whether a Leak Exists describes a technique you can use if you are not sure whether there is a memory leak on your system.
Easy Detection Of Memory Leaks Codeproject
A logic bomb was executed and is responsible for the data transfers.
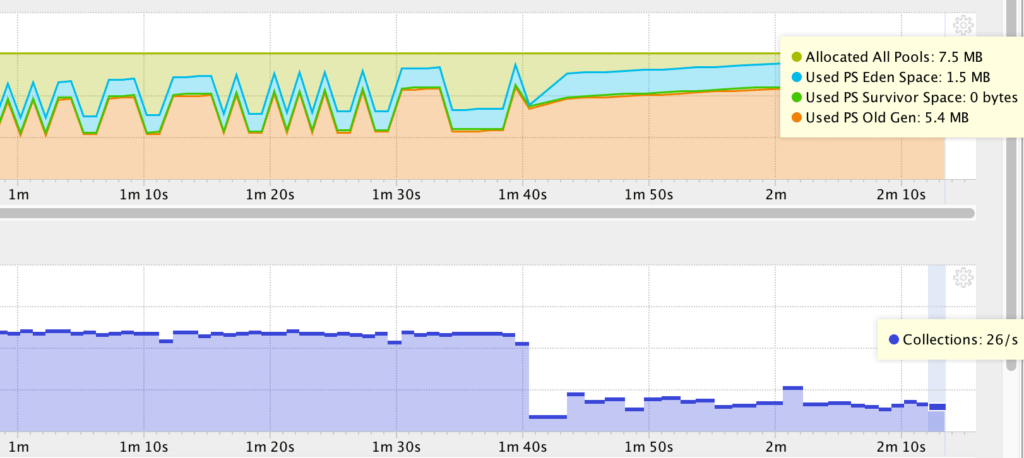
. This section includes the following. Which of the following is the best practice to prevent code injection attacks. As there is no limit placed on the memory usage of the collectd.
Not using Finally block often. So that place is reserved for no reason. Last Updated.
Memorybuffer vulnerability Memory leak. The L1 cache is overwritten. A Denial of Service.
Not using Finally block often. John is conducting a penetration test of a clients network. The file integrity check failed for the attached files.
When multiple systems focus a specific system with a DoS attack. When a file that is too large to fit in a sequential memory location overwrites other. Which best describes the 4 phases of a penetration test.
Which of the following best describe fragmentation. Although the attack resulted in a DoS it was caused by a memory corruption more specifically a memory leak NOT a buffer overflow. Which of the following is the BEST option for Ann to implement.
Exploit escalation attack persistence. Which of the following best describes a memory leak. Starting in MEP 40 the collectd process stores its metrics by default in MapR ES where as in previous versions it wrote directly to OpenTSDB.
Buffer overflows result from writing data beyond expected memory boundaries which can crash a program or allow arbitrary code execution. Use Finally block as much as possible. Get Latest Actual SY0-501 Exams Question and Answers from Passleader.
The consequences of memory leak is that it reduces the performance of the computer by reducing the amount of available memory. A fireless virus is spreading in the local network environment. Release database connection when querying is complete.
The workstations are beaconing to a command-and-control server. Which application-testing technique is the most likely to uncover improper input handling. A QUESTION 740 After a security assessment was performed on the enterprise network it was discovered that.
Ability to resize variables. Due to an unrelated code change in MEP 60 and later a memory leak has been identified in collectds use of the MapR ES client to write to the metrics stream. Memory leak occurs when programmers create a memory in heap and forget to delete it.
Which of the following BEST describes this attack. Eventually in the worst case too much of the available memory may become allocated and all or part of the. The focused network is then bombarded with multiple packets from multiple locations.
Memory leaks take place when users create a memory in heap but forget to erasedelete it. Release instances stored in static tables. 242 Ann a security analyst wants to implement a secure exchange of email.
Finding a Kernel-Mode Memory Leak describes how to find a leak that is caused by a kernel-mode driver or component. If memory is completely depleted failures may result. Which of the terms listed below describes a programming error where an application tries to store a numeric value in a variable that is too small to hold it.
The memory leak occurs when a piece of memory which was previously allocated by the programmer. The company firewall blocked the recipients IP address. The mail gateway prevented the message from being sent to personal email addresses.
The CPU receives an incorrect program counter so it reads and the wrong instruction. Buffer overflow is using more memory than allocated. Thats why this is called the memory leak.
The stack is cleared without the user knowing. Theres nothing in the question suggesting that multiple processes are attempting to access the same resources simultaneously a race condition. It further tells us why.
A RAT was installed and is transferring additional exploit tools. Planning discovery attack report B. The question tells us what is happening.
Heap memory allocated by the user is never freed so it is wasted. Which one of the following causes memory leak. Which of the following is not an advantage of a heap.
3 Both a dangling pointer and a memory leak would result. In case you all forgot a memory leak is when a resource doesnt release memory and it becomes unusable. He is currently gathering infor-.
Then it is not deallocated properly by programmer. Data is written from memory to disk. That memory is no longer in use by the program.
For the memory leak some block of memory may have wasted. 1 A dangling pointer would result a pointer whose value is the address of memory that the program no longer owns. The DLP system flagged the message.
2 A memory leak would result the program would own memory that it could no longer access. Which of the following BEST describes why this message was received. Which of the following best describes a collection of computers that have been compro-mised and are being controlled from one central point.

Windows 11 Releases With Memory Leak Problem Pureinfotech
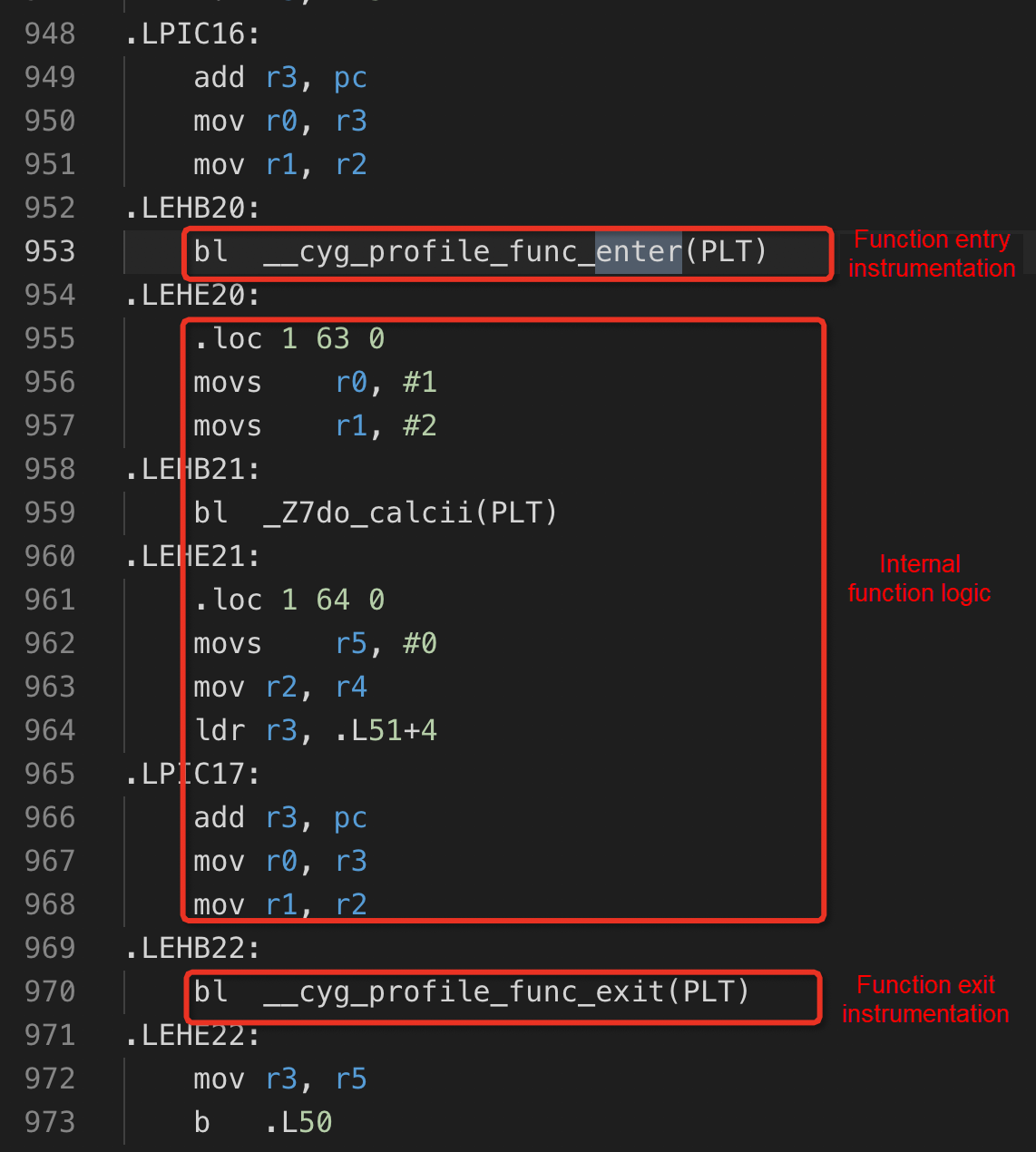
Systematic Solution For Android Native Memory Leak Alibaba Cloud Community
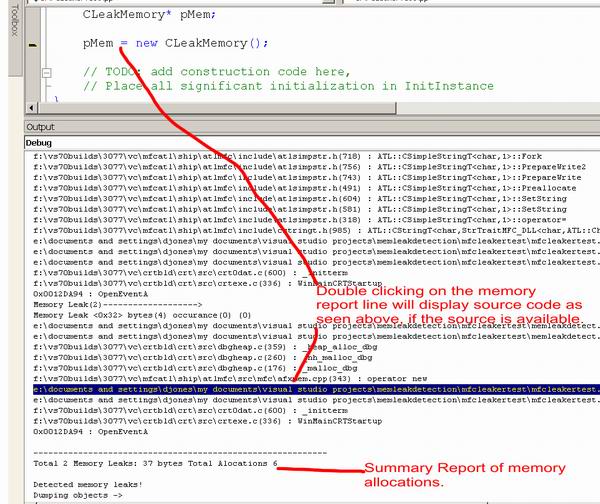
Memory Leak Detection Codeproject
Finding And Fixing Memory Leaks In Python By Peter Karp Buzzfeed Tech
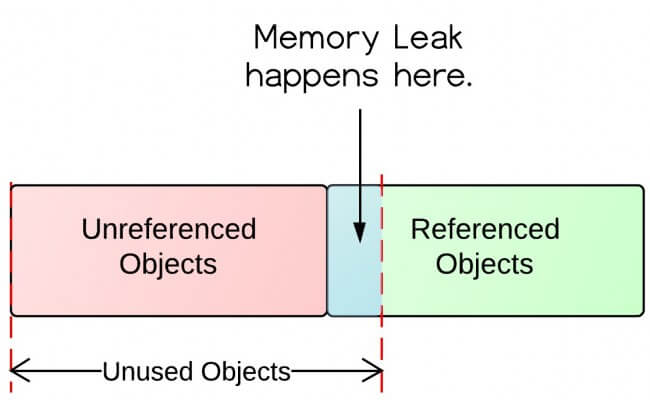
Understand And Prevent Memory Leaks In A Java Application
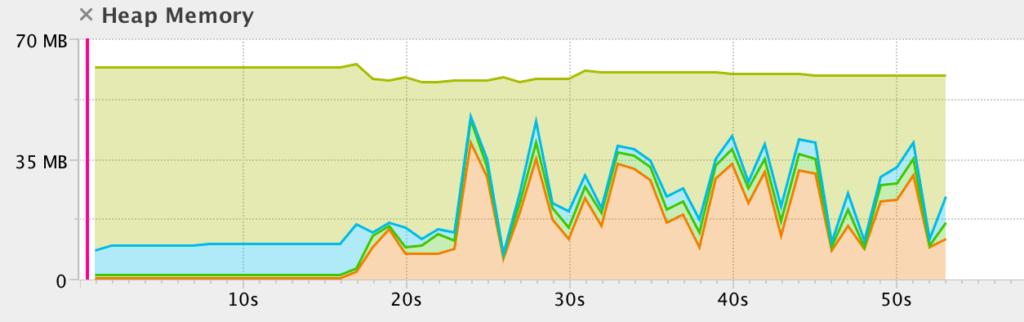
Understand And Prevent Memory Leaks In A Java Application
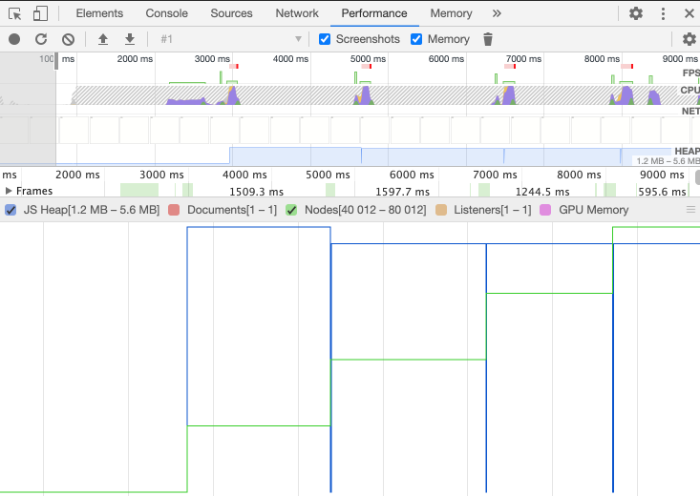
Debugging Javascript Memory Leaks Debugbear
Understand And Prevent Memory Leaks In A Java Application

How To Detect And Prevent Memory Leaks Scout Apm Blog

Understand And Prevent Memory Leaks In A Java Application
Finding And Fixing Memory Leaks In Python By Peter Karp Buzzfeed Tech

What Is A Memory Leak Definition From Techopedia
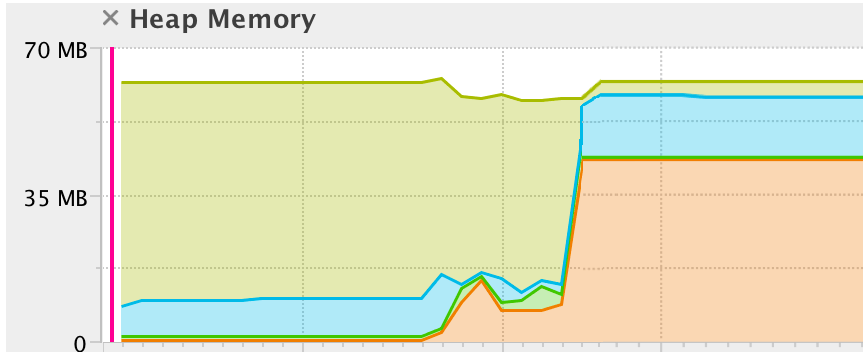
Understand And Prevent Memory Leaks In A Java Application
Finding And Fixing Memory Leaks In Python By Peter Karp Buzzfeed Tech
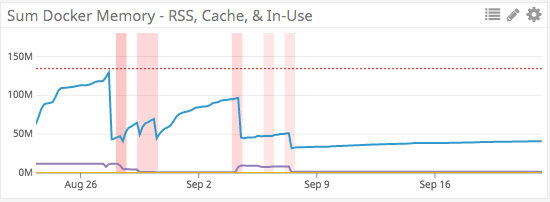
Finding And Fixing Memory Leaks In Python By Peter Karp Buzzfeed Tech
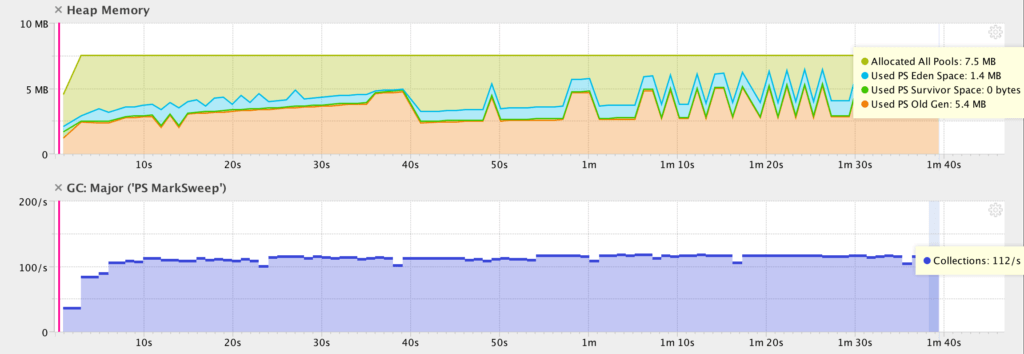
Understand And Prevent Memory Leaks In A Java Application

Ios How To Solve Iphone App Memory Leak In Xcode Instruments Stack Overflow
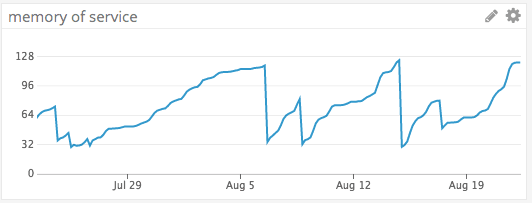
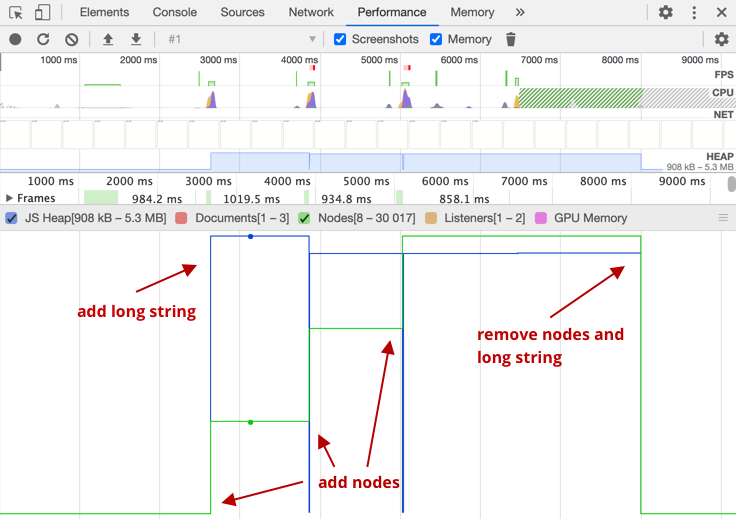
Comments
Post a Comment